Abstract:
A matrix model using three qualifiers (tiers of tool usage; ephemerality of content; social domains of interaction) clarifies the design and evaluation of
courses involving networked components. The model is tool-appropriate, simple enough for instructors to use in their work, and backed up by successful
pedagogical practice.
Content:
Many current models for the design and evaluation of computer-based tools tend to be too complicated for teachers to use, or are based upon assumptions inappropriate to the medium. These shortcomings are particularly noticeable when the models are applied to the design of courses with a networked component. The result is that many projects both fail to significantly enhance the quality of education delivered, as well as lack clear metrics for the evaluation of their achievements. The model I propose here is designed to be simple enough for instructors and other curriculum designers to use effectively, while at the same time rich enough to provide good metrics for effective technological design implementation and evaluation.
A backdrop to the current work is provided by Don Ihde's approach to an applied phenomenology of technology (Don Ihde, Consequences of Phenomenology, 1986; also see the excellent discussion of the application of this theory to programming languages in Bruce J. MacLennan, Principles of Programming Languages, 1999). In Ihde's view, all novel technological tools involve four key dichotomies:
- an ampliative/reductive aspect: this initial dichotomy is present in all tools - a stick used to pick fruit is ampliative inasmuch as it allows access to previously inaccessible food, but reductive inasmuch as it prevents the picker from determining whether the fruit is ripe before picking it.
- a fascination/fear reaction: a direct result from the first dichotomy, the first member of this pair results from utopian focus on ampliative aspects, while the second results from dystopian focus on the reductive aspects.
- an embodiment/otherness component: acceptance of the tool for its ampliative potential leads to practice that makes it an embodied component for the user - the tool in effect becomes transparent to the user. In our previous example, an experienced picker will gradually learn to select ripe fruit from its "feel" through the stick. By contrast, a user that tends to focus on the reductive aspects of the technology will tend to see it as an alien element that never becomes intuitive in its usage.
- a focus/action shift: as a result of the preceding dichotomies, tools influence both focus (how a task is visualized) and action (how a task is executed). A tool affects focus by making some aspects of a task salient, and hiding others (e.g., the stick tends to focus thought on picking individual pieces of fruit, rather than collecting a volume of fruit); it affects action by making some procedures easy, and others difficult (e.g., fruit visible in a straight line is easy to pick with the stick, but fruit nested between branches is difficult to get at).
Just as Don Ihde's work provides us with a clear theoretical backdrop for issues of phenomenology and technology, so we find that the work of Umberto Eco provides valuable insights into issues of signification and communication. One of his simpler models (taken from Umberto Eco, Apocalypse Postponed, 1994) works well for the purposes of the current discussion.
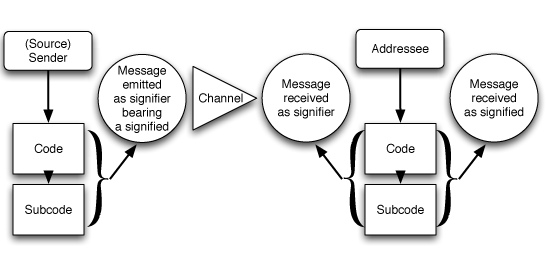
As we can see clearly from this diagram, communication is not "transparent": the code/subcode spaces for the sender and addressee are not one and the same, nor is there a simple identity relationship between signifier and signified in the emitted message and the received message. Thus, the question of the social signifying spaces occupied by sender(s) and receiver(s) in network-mediated tools becomes a crucial one in defining the effectiveness of communication via this tool.
A simple example will help understand the import of Eco's diagram: a surfer, speaking with a lifelong mountain dweller, might say while looking out to sea: "Cool wave, dude." The mountain dweller might then reply: "Aha - I now understand why you always wear that rubber suit." While the surfer and the mountain dweller would share the basic code for "cool", their subcodes would differ, leading the first to express the statement in admiration of the wave as a magnificent surfing opportunity, but the second to receive the connoted meaning as referring to the temperature of the water. In return, the rubber suit, while perceived in similar fashion by both speakers, signifies sporting gear for one, protection from the cold for the other. Neither speaker is stupid, ignorant, or malicious - but it is clear that significant communication has failed to take place here. Technologies designed to mediate communication must address the issues raised by this model, if they are to truly enhance, rather than further obstruct, productive communication.
Ihde's and Eco's theories provide a clear context for the design of implementation strategies for information technologies. However, they do not provide the specifics needed to translate this context into action; the current model aims to provide such specifics.
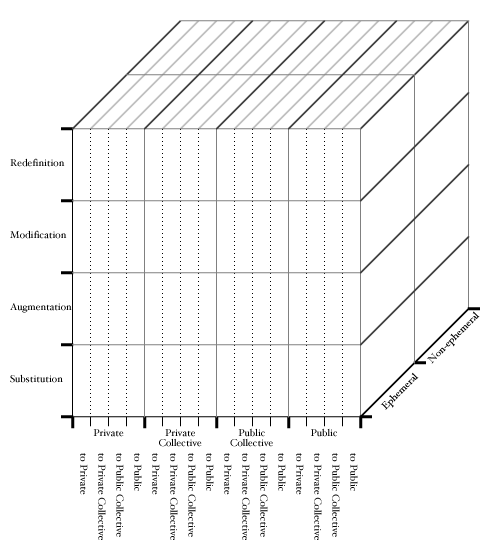
The current model is based upon a three-axis system, defining a cubic grid. The design and evaluation processes are symmetrical: once a course goal has been decided upon, it is mapped to the most appropriate cell in the grid for its definition. This in turn predicates a set of potential technological tools for its implementation. Finally, in an evaluation stage, the parameters defined by the cell selected are mapped back upon actual course results for their evaluation.
The first axis corresponds to a hierarchical set of tiers describing tool usage. I have found this axis to be particularly important in the design of any educational project involving the introduction of computer-based technologies. There are four tiers that occupy this axis:
- Substitution: the computer substitutes for another technological tool, without a significant change in the tool's function.
- Augmentation: the computer replaces another technological tool, with significant functionality increase.
- Modification: the computer allows for the redesign of significant portions of a task to be executed.
- Redefinition: the computer allows for the creation of new tasks, inconceivable without the computer.
It is important to note that no particular "quality" label should be attached to any of the tiers. Thus, the introduction of a Tier I tool rather than a Tier IV tool may be perfectly appropriate, if it best suits the pedagogical goals at hand. What should be clear, however, is that expectations should match the tool usage tier: a Tier I tool cannot provide for new task creation, and design and evaluation metrics should be adjusted accordingly.
The second axis corresponds to the ephemerality of the material to be created and/or shared. There are two possibilities here: the material may be intended as ephemeral (i.e., akin to the communication involved in a classroom discussion or quick blackboard notation) or non-ephemeral (i.e., similar to a structured set of lecture notes or essays). This axis is also quite crucial in the definition of projects: a network tool perceived by students to be ephemeral (such as online discussion groups) is inappropriate for the communication of non-ephemeral material (such as class readings).
The third axis corresponds to the social domains occupied by the sender and receiver of material. Each of these can be private (single author/reader), private collective (selected group of authors or readers), public collective (nonspecific group of responsive authors/readers), or public (nonspecific group of passive authors/readers). A few examples will help clarify each domain: The author of a web page can be viewed as originating a message in a private sphere, placing it for view in a public sphere; a personal email can be viewed as both originating and being received in a private sphere. A weblog can be viewed as originating in a private sphere, but being received in a public collective sphere, where readers can in turn post comments, relink into their own weblogs, etc. Messages posted to a listserver originate in the private sphere, and are received in a private collective sphere. Chatrooms both originate and are received in a public collective sphere.
For visualization purposes, the resulting model can be viewed as a cube: